
Zero Trust and AI
Where AI stands in Zero Trust Security?
Is AI an advantage for Zero Trust Security or a disadvantage?

What is Remote Browser Isolation
What is Remote Desktop Isolation
Do you hesitate to click suspicious links? Don't hesitate, click it in our world.

Split Web Traffic
How to split your web traffic with our ZTNA solution
We will send some of our client web traffic over our ZTNA to the internet

A new VPN over QUIC protocol with Rust
QUIC protocol benefits for VPN
A new free open source business VPN for everyone
What is Zero Trust Network Access?
A new security framework against traditional trusted models.
Difference between VPN and ZTNA

OpenVPN Alternative
Open source alternative to OpenVPN that is designed with Zero Trust Principles
A new free open source business VPN for everyone
What is Applications Network
Is zero trust network means applications network?
Creating a network of applications, not computers are an interesting solution
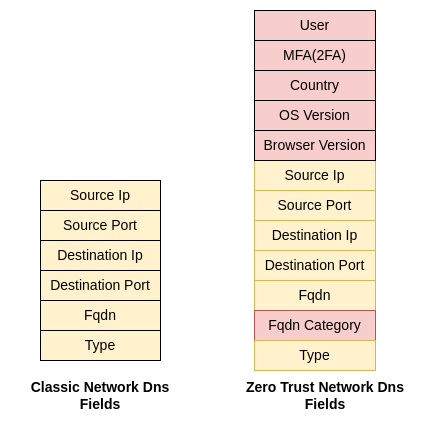
Dns Log Analysis In A Zero Trust Network
How dns log is different in a zero trust network
What is the difference from a classic network
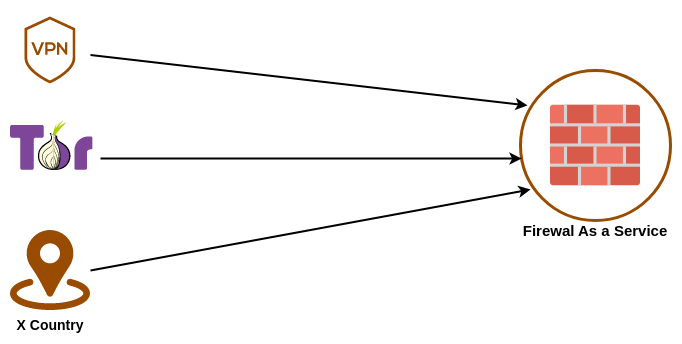
Ip Intelligence
What is ip intelligence in zero trust architecture.
It's role and benefits for zero trust access
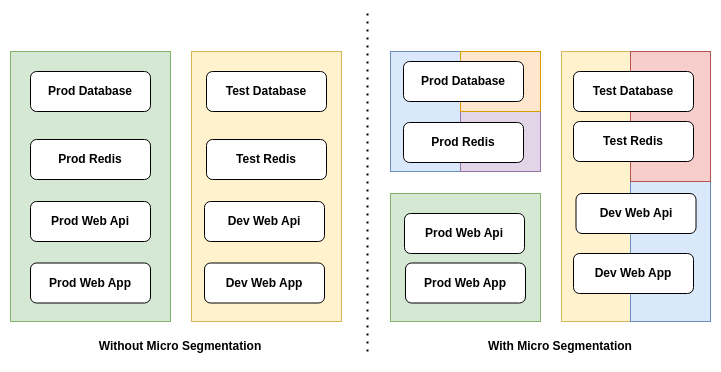
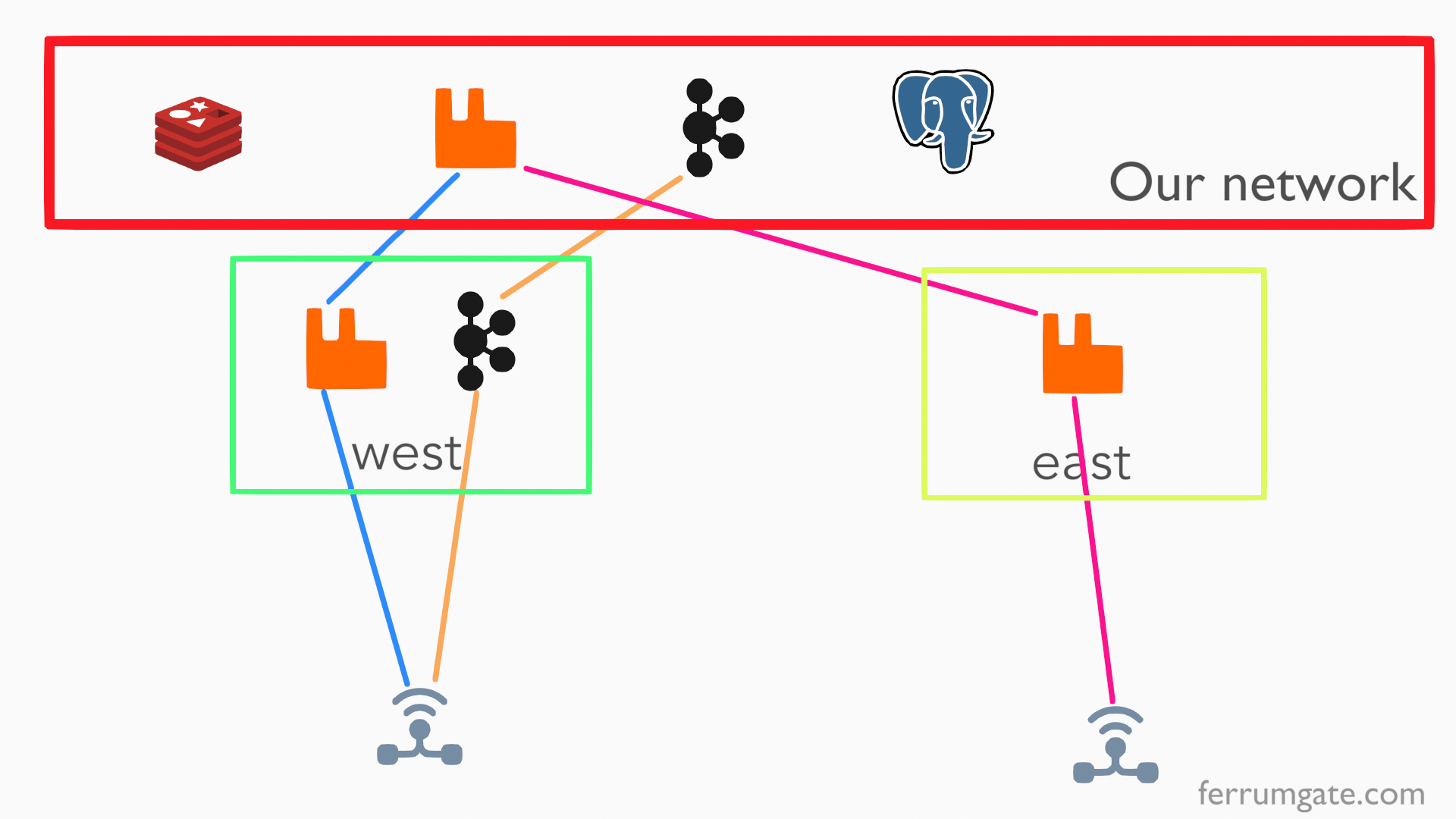
Zero Trust Access - Micro-Segmentation
What is micro-segmentation in zero trust access (ZTA)
A real example of zero trust micro-segmentation
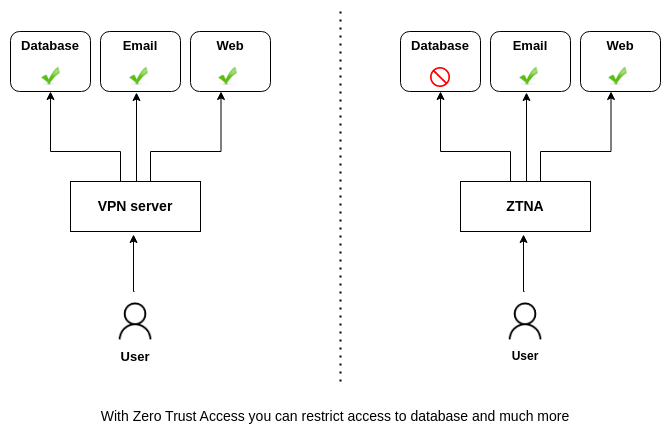
Zero Trust Network Access (ZTNA) vs VPN
What makes different ZTNA (Zero Trust Network Access) from traditional VPN (Virtual Private Network)
What is the purpose of Zero Trust Network Access
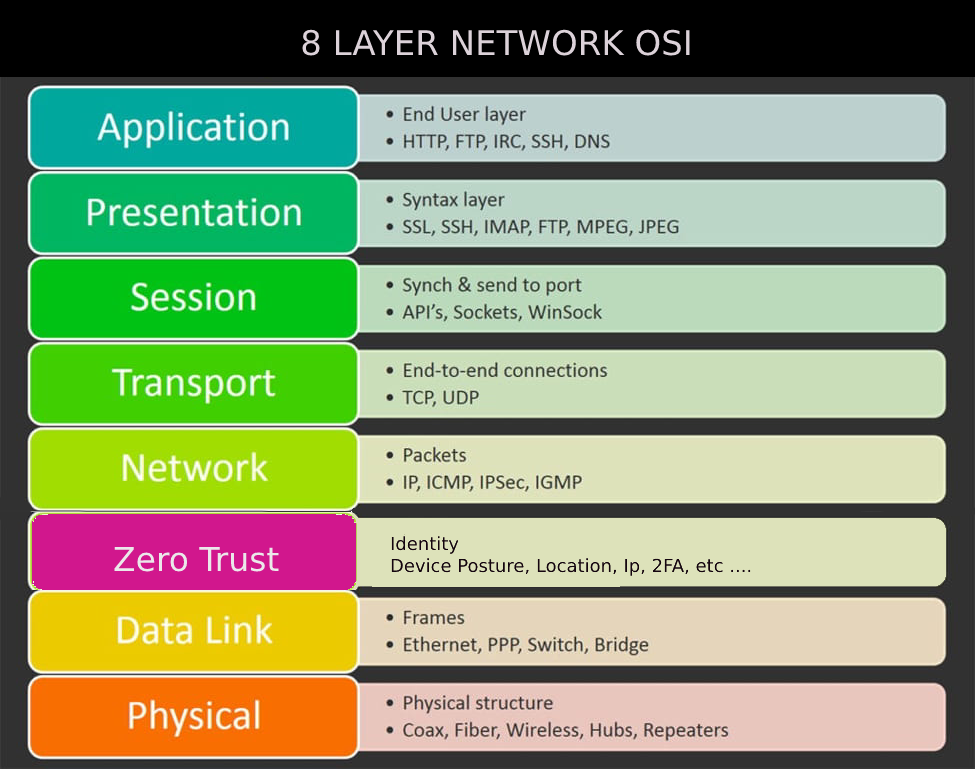
New Network OSI Model For Zero Trust Security
FerrumGate implements its zero trust networks by adding a new layer to network OSI layer
Adding a new layer, changes so many things for next generation cybersecurity...
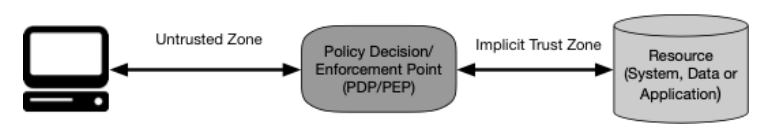
Zero Trust Architecture
Zero Trust is the term for evolving cybersecurity paradigms
Zero Trust assumes there is no implicit trust...
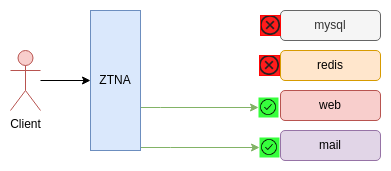
Forget Private Network, DMZ, VLAN, Classic Firewall
A new design for zero trust
FerrumGate implements a Zero Trust Model...