Forget Private Network, DMZ, VLAN, Classic Firewall
Jan 17 2023
Zero Trust Model
Zero Trust model includes several key components
-
Identity and access management: Every user and device must be authenticated before being granted access to resources. This can include multi-factor authentication, device health checks, and user behavioral analysis
-
Micro-segmentation: The network is divided into small segments, with each segment containing only the resources that a user or device needs to perform its intended function.
-
Least privilege access: Users and devices are granted the least amount of access necessary to perform their intended function.
-
Continuous monitoring: Network traffic is continuously monitored for suspicious activity, and any anomalies are flagged for further investigation.
There is a little problem, with implementing Zero Trust policy for the current network design
Network packets do not have an authentication header, packets have only TCP/UDP/IP headers with these headers, writing security rules is limited
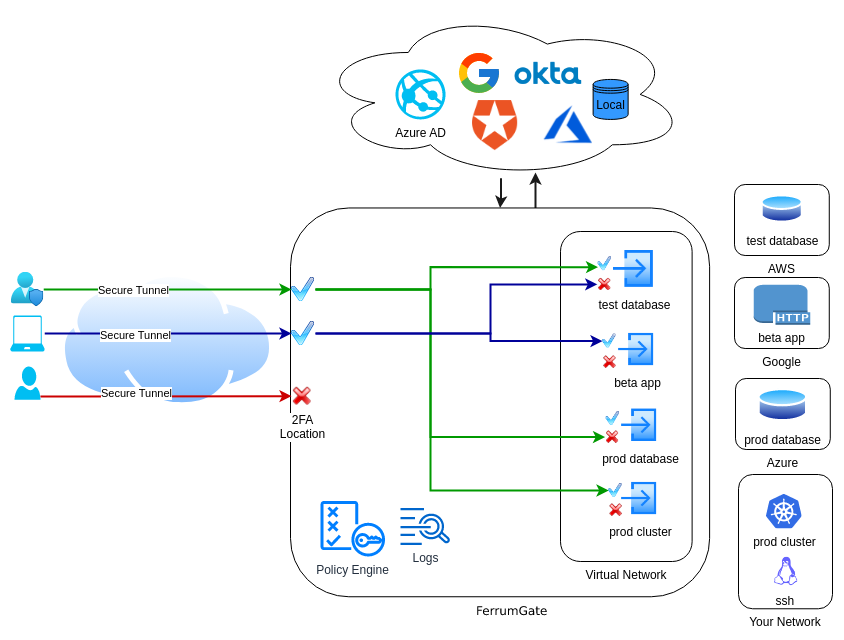
FerrumGate Zero Trust Virtual Network Authentication
FerrumGate implements a Zero Trust Model successfully
First of all, every user or device is checked before connecting to the network
FerrumGate supports all authentication methods like (more)
- Local
- OAuth2
- Saml
- Local
- Active Directory
- Google Workspace
- Azure AD
- etc...
and device postures, ip filtering, location filtering and etc...
After authentication we know lots of information about packets that flows in our virtual Zero Trust network (more)
Monitoring
FerrumGate logs every allowed or denied request
Logs are more detailed than a Firewall, who, when, why, from, to, and result questions are answered
Conclusion
FerrumGate is new software defined virtual network for Zero Trust that succeeds
-
Identity and access management
-
Micro-segmentation
-
Least privilege access
-
Continuous monitoring