Dns Log Analysis In A Zero Trust Network
Mar 17 2023
What is DNS?
DNS is probably one of the oldest protocols in computer history. It is nearly the same as it developed first. It just translates fqdn to an IP address. It is just a translator, with a big role in the internet. It is not encrypted, all of your visited websites are seen, router to ISP to DNS resolver like google, Cloudflare, or else. Everyone sees which sites you are visiting. By using DOH you can encrypt your DNS traffic, but the DNS resolver sees all your traffic. Also, data integrity is another problem. With DNSSEC data integrity is resolved, but DNSSEC is not mostly used now.
DNS Fields
Most important fields of the DNS according to security
- Fqdn what is the full name of a host
- Query Type What is the recourse type like ip address IPV4, IPV6, or MX like mail record, TXT record for validating something
How we can use this fields for security? - Fqdn
Every fqdn is related to at least one category like Phishing, Technology, Shopping, Social network, Malware, and Hacking. If you know the domain category, you can block access to that site. This depends on Domain Intelligence you have. Also analyzing fqdn for DGA(Domain Generation Algorithm) is important. Analyzing fqdn for DNS Tunneling is another point.
- Query Type There is a relation between query types in a network. Following that statistics is a good point for anomaly detection.
Every fqdn is related to at least one category like Phishing, Technology, Shopping, Social network, Malware, and Hacking. If you know the domain category, you can block access to that site. This depends on Domain Intelligence you have. Also analyzing fqdn for DGA(Domain Generation Algorithm) is important. Analyzing fqdn for DNS Tunneling is another point.
Dns Fields
| Field | Example |
|---|---|
| Source Ip | 192.168.1.10 |
| Source Port | 33456 |
| Destination Ip | 1.1.1.1 |
| Destination Port | 53 |
| Fqdn | www.google.com |
| Type | IPV4 |
| Field | Example |
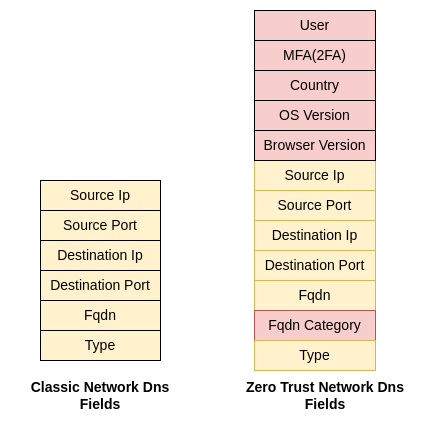
|---|---|
| User | abc@def.com |
| MFA | 2FA verified |
| Country | US |
| OS Version | Windows 10 |
| Browser Version | Chrome 111 |
| Source Ip | 192.168.1.10 |
| Source Port | 33456 |
| Destination Ip | 1.1.1.1 |
| Destination Port | 53 |
| Fqdn | www.google.com |
| Fqdn Category | Technology |
| Type | IPV4 |
Benefits
With more fields for a dns request. You have more control over dns protocol. Just block harmful fqdns and limit attack surface. Also with more fields, AI engines can detect harmful attacks more pricesly.