OpenVPN Alternative - Open Source Zero Trust Network Access
May 15 2023
How OpenVPN works?
OpenVPN is a traditional VPN provider. It creates a secure and encrypted channel over the internet between remote users and private networks. The problem in this model is accessing the private network.
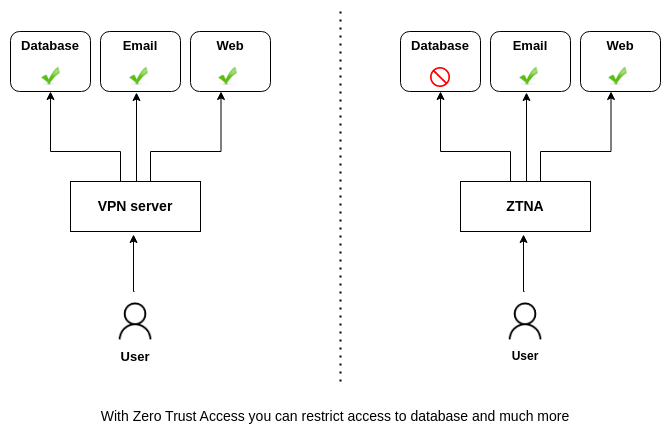
For connecting it supports some IdP providers. But authorization is absent. After connection, everyone can access to all private network resources.
This feature is not a good cyber security practice. Accessing or chance to access resources is a little problem. Because of this Zero Trust Network Access (ZTNA) is the new approach.
What is Zero Trust Network Access?
Zero trust network access (ZTNA) is a security framework that aims to provide access to applications without network-based trust models. ZTNA products main feature is authorization. ZTNA defines accessing applications, as not accessing networks. The main key is accessing applications.
Our features against OpenVPN
We have lots of features for secure access
-
Identity and access management
We are supporting Local, SAML, OAuth2, and MFA(multi-factor authentication), or passwordless access.
Just use our local database or Google, Okta, Github, etc...
Check access ip against blacklists, whitelists, VPN, and tor IPs.Limit access from countries.
Limit access between working hours
Check device postures before access
-
Don't trust, always verify
We are always checking who can access to what and when.
You can say that user X can access the database but user Y cannot access the database.
-
Micro-segmentation
You can define your resources as services. We call resources, services. Separate each resource as you want.
Define your database as a service, RDP service on a server as a new service, Or ssh service on the same machine. Micro-Segmentation as you want.
-
Least privilege access
Give only users what they need, not more.
You can say that user X can access DNS but cannot access social web pages. DNS filtering works.
A user can access Database but can not drop it.
A user can access RDP, but cannot copy files.
-
Continuous monitoring
Watch everything in your network. Follow every packet in the network flow.