How to Split Client Web Traffic
Sep 28 2023
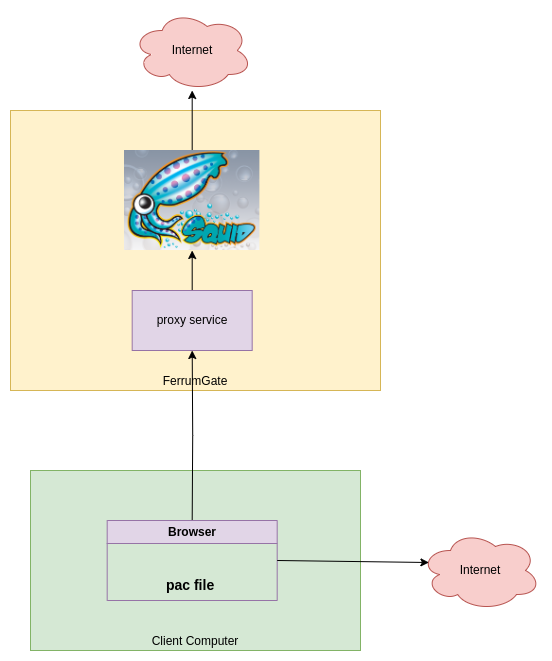
We want to send some of the client web traffic over ZTNA to the internet!
As you know our ZTNA splits network traffic which means does not send all traffic to ZTNA. Only forwards the related traffic to internal resources is allowed. But if you have a SaaS service that is protected by your public IP like Office365 or others? How can we fix it?
Scenario?
We want our clients must access to bbc.com by using our squid server. In this way, the destination will see the ZTNA public IP address as accessing. All other traffic will use the client's internet.
Please follow the below steps.
Clients can use our ZTNA to access bbc.com only.
Configuration
-
On the host terminal, let's add a new ip address to lo the interface
ip addr add 10.100.100.10/32 dev lo #### for permanent #### be carefull below changing, you are warned #### some systems use different network management cp /etc/network/interfaces /etc/network/interfaces.backup echo " auto lo:0 iface lo:0 inet static address 10.100.100.10 netmask 255.255.255.255 dns-nameservers 1.1.1.1" >> /etc/network/interfaces -
install squid proxy
apt install -y squid -
hardening squid security - change listen ip to 10.100.100.10
cp /etc/squid/squid.conf /etc/squid/squid.conf.backup ###add ip:port listening sed -i 's/http_port 3128/http_port 10.100.100.10:3128/g' /etc/squid/squid.conf ### disable localnet only ferrumgate networks sed -i 's/acl localnet src/#acl localnet src/g' /etc/squid/squid.conf sed -i 's|#acl localnet src 10.0.0.0/8|acl localnet src 10.10.0.0/16|g' /etc/squid/squid.conf sed -i 's|#acl localnet src 0.0.0.1-0.255.255.255|acl localnet src 0.0.0.1-0.255.255.255|g' /etc/squid/squid.conf -
create proxy whitelist domains
mkdir -p /usr/local/share/ferrumgate echo " .office.com .office365.com .outlook.com .bbc.com " > /usr/local/share/ferrumgate/whitelist -
prepare squid access
#### squid accepts connections only from ferrumgate networks #### and only to whitelist domains sed -i '/^#http_access allow localnet/i acl whitelist dstdomain "/usr/local/share/ferrumgate/whitelist"' /etc/squid/squid.conf sed -i 's/#http_access allow localnet/http_access allow localnet whitelist/g' /etc/squid/squid.conf -
restart squid
systemctl restart squid -
create a pac.js file for proxy settings
mkdir -p /usr/local/share/ferrumgate/private/proxy echo " function FindProxyForURL(url, host) { if ( shExpMatch(host, \"outlook.office.com\") || shExpMatch(host, \"*.outlook.office.com\") || shExpMatch(host, \"office365.com\") || shExpMatch(host, \"*.office365.com\") || shExpMatch(host, \"*.outlook.com\") || shExpMatch(host, \"*.protection.outlook.com\") || shExpMatch(host, \"bbc.com\") || shExpMatch(host, \"*.bbc.com\") || shExpMatch(host, \"youtube.com\") || shExpMatch(host, \"*.youtube.com\") ) { return \"PROXY proxy:3128;DIRECT\"; } return \"DIRECT\"; }"> /usr/local/share/ferrumgate/private/proxy/pac.js -
open the FerrumGate management portal, and create a service like below,
this service will give us pac file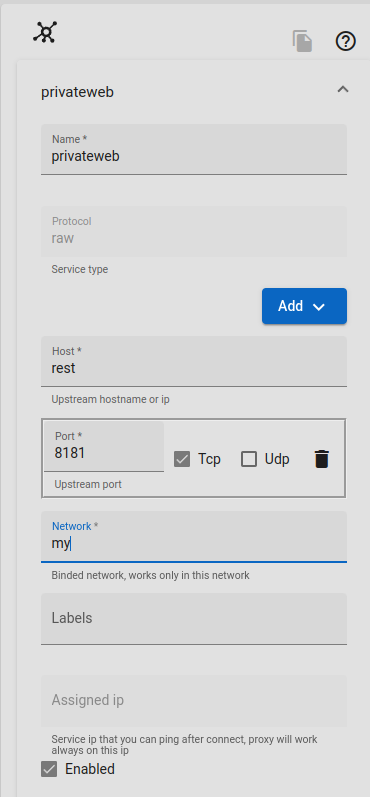
-
create a service like below
this service will control access to the squid proxy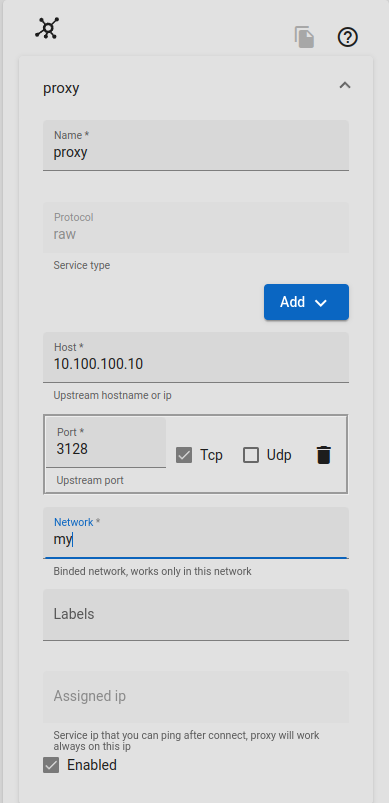
-
give permission to services from Policy/Authorization
-
open your proxy settings, set to automatic and paste below
http://privateweb:8181/share/private/proxy/pac.js -
Check it works, after restarting the browser
bbc.com will be open
youtube.com will not open
amazon.com will be open
-
Troubleshoot
Restart browser
Connect ZTNA and open this URL http://privateweb:8181/share/private/proxy/pac.js
Check file /usr/local/share/ferrumgate/whitelist
Check file /usr/local/share/ferrumgate/private/proxy/pac.js
Check http://proxy:3128/