Zero Trust Architecture
Jan 27 2023
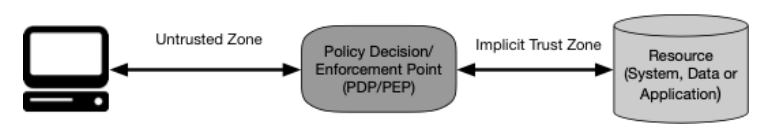 Figure 1: Zero Trust Access. Source: NIST SP 800-207
Figure 1: Zero Trust Access. Source: NIST SP 800-207
Don't trust
Zero Trust (ZT) is the evolving cybersecurity paradigm that moves from defencing networks to resources. A new network design beyond private networks, DMZ . Zero Trust focuses on protecting resources (assets, services, workflows, etc). Zero Trust assumes that there is no implicit trust in assets and users based on anything. Authentication (Authn) and Authorization (Authz) are key functions in Zero Trust
Zero Trust Architecture (ZTA)
Zero Trust Architecture (ZTA) is a cybersecurity architecture that is based on zero trust principles and designed to prevent data breaches and limit movement in the network. ZT is not a single architecture, but a set of guidelines for achieving security. On this journey, many enterprise networks will operate in a hybrid zero trust/perimeter-based mode, while continuing. When balanced with existing security policies, identity and access management,and continuous monitoring, ZTA can protect against common threats and improve security posture by using a managed risk approach
-
Focus on resource protection
-
Don't trust, verify every access
-
Least privilege access to any resource
-
Continuous monitoring
Tenets of Zero Trust
-
All data sources and computing services are considered resources. A web app or a database or redis or software as a service or a file are whole resources.
-
All communication is secured regardless of network location. All communication must be secure aware of location, like from a cafe or in company or from a beach. In other words, every connection must meet the same criteria for security. Every request is the same aware of the location
-
Access to individual enterprise resources is granted on a per-session basis. Before access, evaluate the trust. And access should be granted with the least privileges. Authentication and authorization to one resource will not automatically grant access to a different resource.
-
Access to resources is determined by dynamic policy. An organization defines what resources it has, who its members are. and what access to resources those members need. For zero trust, asset state is also important, such as software versions installed, browser version, OS version, network location, time/date, previously behavior. These rules and attributes are based on the needs.
-
All resource authentication and authorization are dynamic and strictly enforced before access is allowed.Trust before access, and continually reeavulating trust in ongoing communication.
-
The enterprise collects as much information as possible about the current state of assets, network infrastructure, and communications and uses it to improve its security posture.Collect all possible data and process that data for better security.