Zero Trust Micro-Segmentation
Feb 27 2023
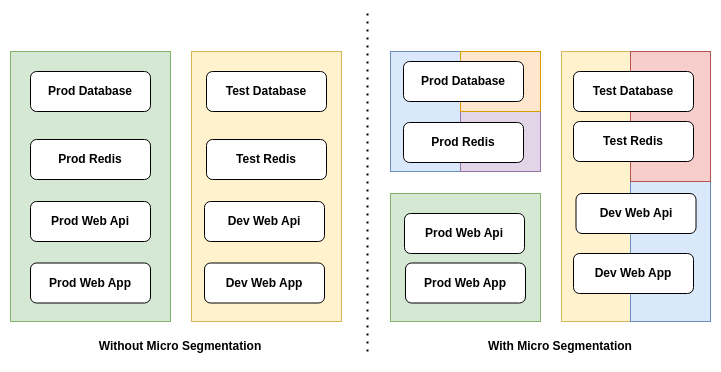
What is micro-segmentation?
Zero Trust is a security model and micro-segmentation is a best practice for minimizing the attack surface. Segmentation is a term for grouping some resources.
Grouping hosts on a network is a segmentation example, and development servers grouping is a segmentation example, but micro-segmentation must be a little bit small, and grouping applications, not servers is a good micro-segmentation example.
How traditional networks works?
Today's networks are simple, there are servers and these servers serves some applications like database, web app, email server, file server, redis, elasticsearch, etc... When you connect to a network, it is possible to reach any app. Why this happens like this because traditional segmentation depends on mostly hosts. Today's segmentation is done with VLANs and firewalls. Creating and managing lots of VLANs is a tricky problem.
What we need?
Segmentation over applications is a good practice. For the best practice, grouping applications and creating a micro-segmentation zone is what we need. Suppose grouping development redis, database, web application is an example. Or grouping HR resources is another example. Creating micro-segments minimizes attack surface. By reducing the attack surface, you will be able to implement the best policy management.
Benefits
- Minimizes attack surface
- Custom policy management
- More control
- More visibility
FerrumGate solution
With FerrumGate implementation, you will be able to create applications network
You can group applications and create networks as you want, there is no limit to creating networks. You can create a network for an application or more. Also, you can use the same application on multiple networks.