ZTNA (Zero Trust Network Access) vs VPN (Virtual Private Network)
Feb 15 2023
Why we need VPN?
Today's workplaces are flexible, and users can work from home, or another city or they can be
There is no way to open these applications to the internet safely. That will bring to you new security challenges to solve. Because of security concerns, you need a technology like VPN, to connect remote users or applications to these resources. With VPN, without opening all resources to the internet, remote users can connect to your network resources.
How VPN works?
When you create a VPN connection to a destination, this means that some of your network traffic or all of your network traffic is routed to that destination.This always succeeds by creating encrypted, secure tunnels. This also means your traffic is secured and only seen in VPN provider. When a VPN connection is created, you see no difference between your local network and corporate network. You can reach your corporate network resources like local network resources.
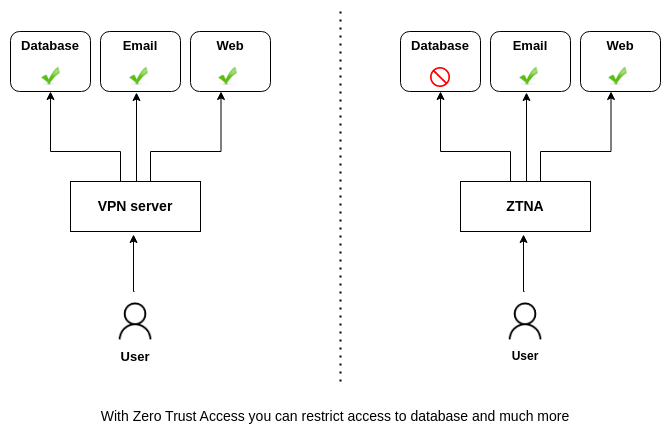
The problem
When you use a traditional VPN, when an account is compromised, the attacker can reach all resources in your network. This means the attacker can scan your network, can detect your servers, your databases, your all resources, and their vulnerabilities. After that nightmare starts.
This is all caused because of a trusted user, that is connected to your network over traditional VPN.
Do you think, every connected user is trusted?
The solution is ZTNA
For solving this kind of problems, you must apply Zero Trust principles
- Identity and access management
To connect to a resource, you need a strong identity and access management system. It must support Local, SAML, OAuth2, and MFA(multi-factor authentication), or passwordless access.
- Don't trust, always verify
When you want to reach a resource like a database, in ZTNA if you are not allowed, there is no way to reach that resource. Every request is always checked, if allowed then you can reach
- Micro-segmentation
Every resource must be defined seperately. For example access to a database, access to a rdp service, access to a ssh service, access to a file, etc... must be isolated from each other.
- Least privilege access
Users can only reach what they need. If user needs to use only a stock web app, then give this permission only, nothing more.
- Continuous monitoring
You need to monitor every request to every resource always, and must take action, system must be dynamic.
FerrumGate ZTNA solution
FerrumGate applies all zero trust principles, with addition more features