ZTNA vs VPN
Dec 28 2023
More Authentication Options ?
Zero Trust Architecture is a security model that emphasizes the importance of authentication (AUTHN) and authorization (AUTHZ). In order to access a resource such as a database, file service, or file download, authentication is required first. Once authenticated, you can connect to the Zero Trust Network Access (ZTNA) which supports multiple authentication options such as SAML, OAUTH2, LDAP, and all other authentication protocols.
- MFA(Multi Factor Authentication) Check
MFA is the default feature of ZTNA, you can be forced to use MFA in the whole system.
- Location Check
When you want to connect, ZTNA can check your ip information like country, and if ip belongs to a tor network, or from a proxy, by this information you can limit connections, and you can set new policy rules.
- Time Check
When you want to connect, ZTNA can check timezone and give permission or deny it. Suppose you can give access only working hours and days.
- Device Posture Check
With device posture checking, you can limit devices according to operating system upgrades, check MAC address, check antivirus, and more
- More Functionality
With ZTNA you can add new authentication methods like fingerprint recognition, face recognition, and many more.
One of the most important expressions in ZTA(Zero Trust Architecture) is "mitigating attack surface". With enhanced rules, you can mitigate attack surfaces.
Micro Segmentation?
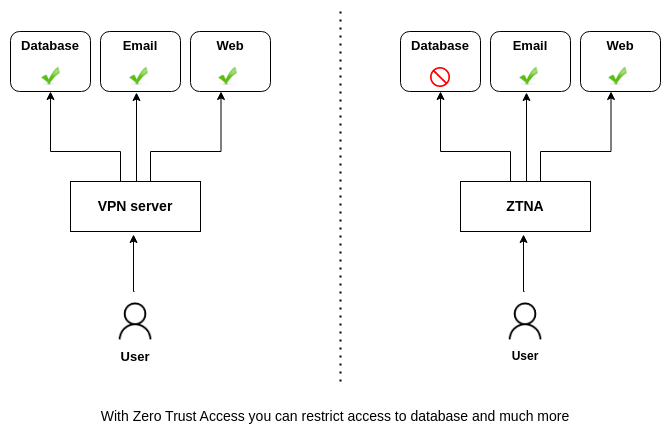
If the user connects with old VPN technology, how can you protect a database from this unrelated user?
You need to create new VLANs. A VLAN for accountants, a VLAN for developers, a VLAN for sales, a VLAN for remote workers, this goes on like this. With ZTNA segmentation methods, you can easily create Virtual Application Networks (VAN) without any changes to your network. In this way, only relevant users can access relevant resources.
Least Privilege?
This rule defines, giving users only what they need, not much not less.
If the user is irrelevant to an RDP service, then the user cannot reach that service if knows either the password. In this way, you can mitigate the attack surface.
If the user has access to a database, Do you need to give access to the "Customer" table? Do you need to give "truncate table" permission?
Continuous Monitoring?
All ZTNAs must follow every packet, every flow, and every connection. If policy changes, ZTNA must be able to close the connection. This feature is a must-must rule.
If you recognize that an attacker is in your system, ZTNA must be able to cut off connections from the attacker.