How it works
Let's explain what this picture means.
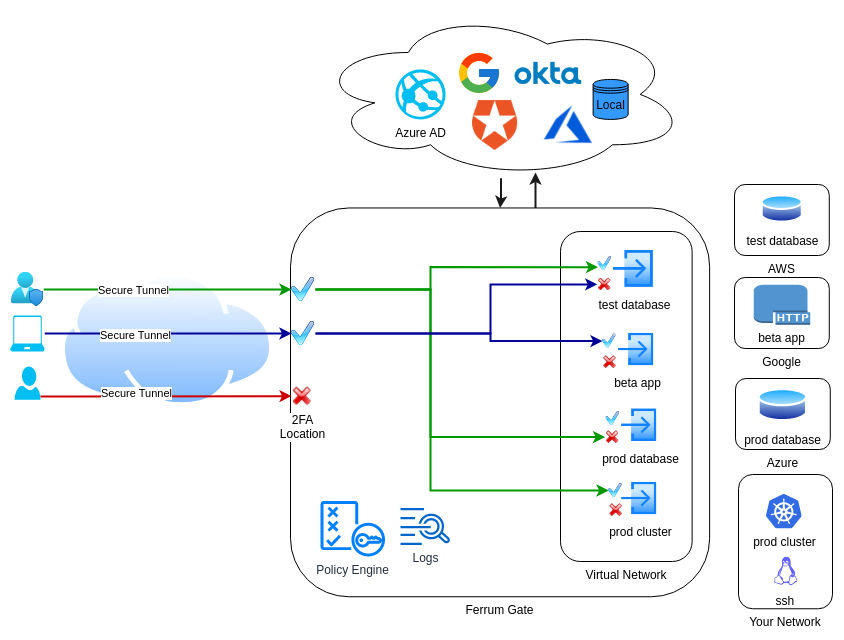
FerrumGate works like a Zero Trust switch or gateway.
Clients (real users, phone, computers, IOT devices etc...) tries to connect the FerrumGate server, then policy authentication engine checks client from configured auth sources like Google, LinkedIn, Azure AD, local etc... then through location, ip, time,device posture etc..., if everything is ok then engine allows to create a secure tunnel to virtual network. This is like plug your ethernet cable to Zero Trust virtual network.
when client tries to reach a service(a resource like mysql server), policy authorization, checks the rules if everything is ok, like checking 2FA, service specific fields like http post, http get or nfs file path or dns query then allows or denies the request at network packet level.
By the way, every thing is denied, you can allow what you want.