IP Intelligence Settings
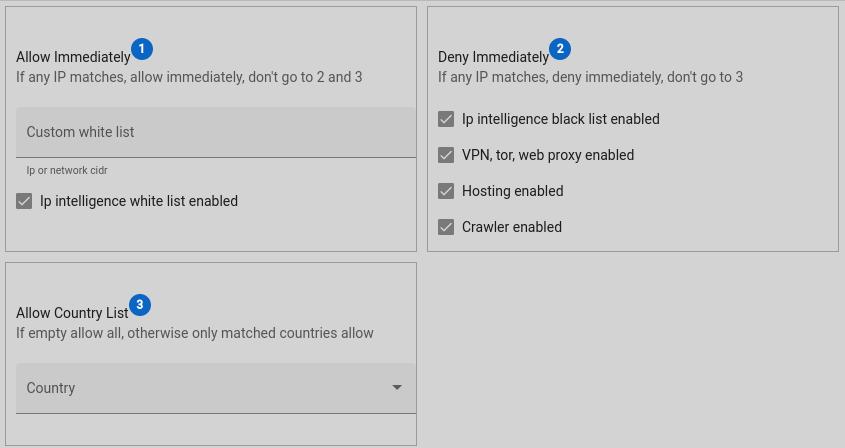
Limiting authentication, accessing to your networks via ip intelligence, mitigating attack surface by ip is a good strategy.
VPN, Tor, Proxy, Ips
Some attackers tries to be anonymous over vpn, tor, proxy ips. Blocking these ips will be a good strategy
Hosting Ips
These are hosting company ips like AWS, Google, Azure etc. Some attackers may open a custom vpn for themselves via hosting companies. Blocking these ips will be a good strategy.
Crawler Ips
Some companies are crawling internet for their purposes. Normally there is no risk about these ips.
Sources
We already added some providers, create an account and app Api key. If you need extra providers, just send us email, contact over community or contact over discord community.
Warning
When you create a subscription, there are some options on these providers. If you want to block VPN, Tor, Proxy IPs, then you need to select a suitable plan, otherwise you won't be able to use these features.
Blacklist
Add network cidr block, if you want to deny access from that blocks
Whitelist
Add network cidr block, if you want to allow access from that blocks