PKI Settings
We are supporting PKI (Public Key Infrastructure), for TLS Connection, Authentication with Certificates and TLS Inspection. We follow the classic path, We use 3 Layered model. CA Certificate, Intermediate Certificates and General Certificates.
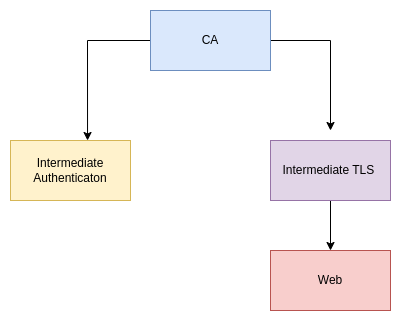
CA
There is a root CA certificate, that is created automatically when the system is installed. This stands at the top.
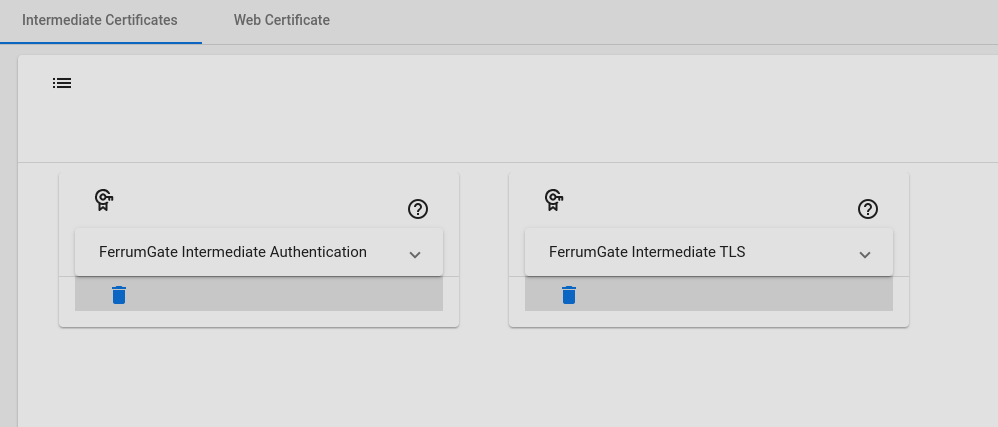
Intermediate Authentication
As you know, authentication with certificates is a good practice, especially for IOT devices or applications. When the system is installed, automatically an Intermediate certificate is created. You can create more with Add button for logical grouping. For example, you can create certificates for different regions. And you can use these certificates at user's login methods to create an authentication certificate. Remember if you delete an intermedia certificate, all certificates will be invalid which are signed with this deleted certificate.
Intermediate TLS
This certificate is also created when the system is installed. We are using it for signing web certificates or other TLS needs. For example for secure communication to services. For securing service communication, we can create a certificate, and make it more secure. For the web gateway, we need TLS inspection, we will create new certificates from these certificates.
Web
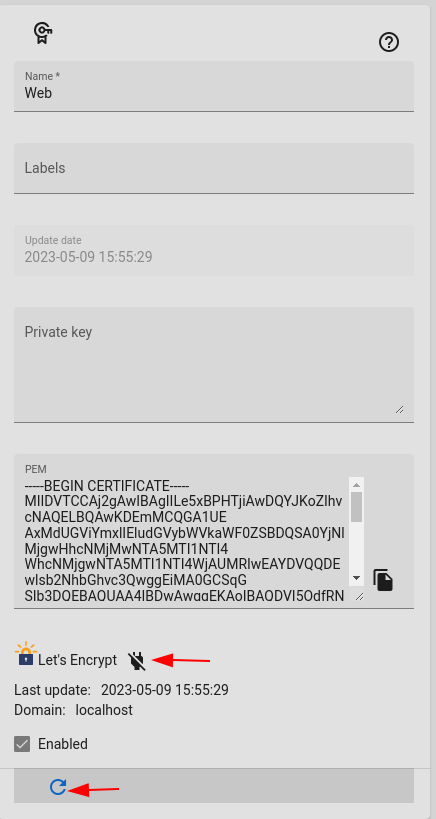
This is the portal page certificate which signed by Intermediate TLS, for web. This certificate is domain comes from $url variable from common/login. Also you can upload your certificate. And you can get from let's encrypt.
Let's Encrypt
And you can get a certificate from let's encrypt. Just click let's encrypt enable button for getting a new one. Remembers domain comes from $url variable from common/login.
Warning
Web server 80 post must be accessible from internet.
Warning
There is no automatic renew, for renew just click refresh button before 90 days. Let's encrypt signs for 90 days.
Warning
Client program can not verify Let's Encrypt certificates. Uncheck verify from options, restart and try again
For error debugging on server bash
``` sh
docker logs -f $(docker ps| grep rest.portal|cut -d' ' -f1)
```
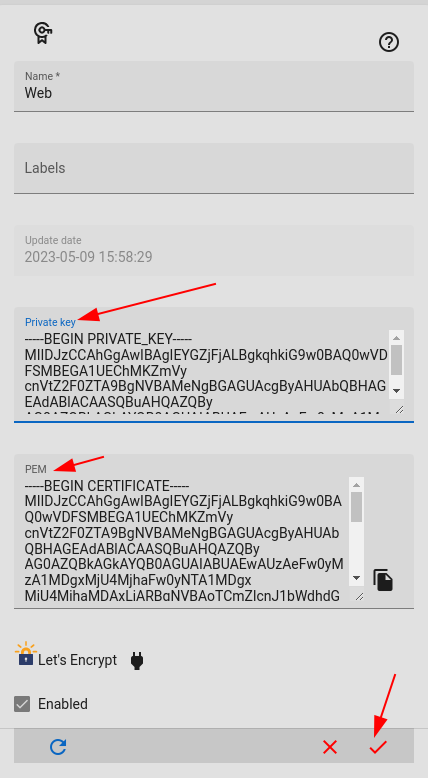
Loading Custom Web Certificate
You can load your custom certificate from pem format. Just paste private and public keys and save it.
Manuel Certificate Copy
You can copy your certificates to host folder /var/lib/docker/volumes/fg-base_ferrum/_data/certs/ file names must be private.key , and public.crt, you can copy pem or crt files. After copy, you need set permissions to files with below