Open Source ZTNA
Apr 6 2023
Remote Access?
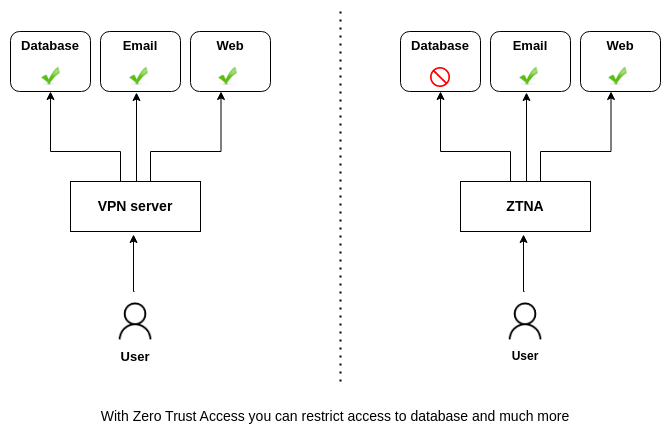
One of our use cases is remote access for workforces. In recent years, companies are choosing remote work. In the future, probably everyone will work remotely. Until recent years, for remote connectivity, everyone used VPN technology.
This is the case, why we need a more secure access solution according to VPN. VPN connectivity is secure, but just the connection is secure, and access to resources is not secure. In one of our previous blogs, we analyzed the differences between ZTNA vs VPN in this blog. Take a look. Because of this, we need a Zero Trust Network Access (ZTNA) solution.
What is ZTNA?
Zero Trust Network Access is the new security paradigm vs to VPN access. And in one of our previous blogs, we described it as zero trust network access as grouping applications as new networks. Grouping applications and creating new software-defined networks (SDN) with them. Also, we can say this type of networking, is software-defined perimeter (SDP).
There is also Zero Trust Access (ZTA). ZTA and ZTNA are two different concepts. Although they share some similarities and are often used interchangeably.
ZTA is a security framework, that involves a comprehensive approach to access control, including not only network access. But also access to applications, data, and other resources where they are located on-premises or in the cloud.
ZTNA is a specific implementation of ZTA that focuses on securing remote access to resources.
Features
- No change requires at your network
Just install software on a premise with the following instructions .
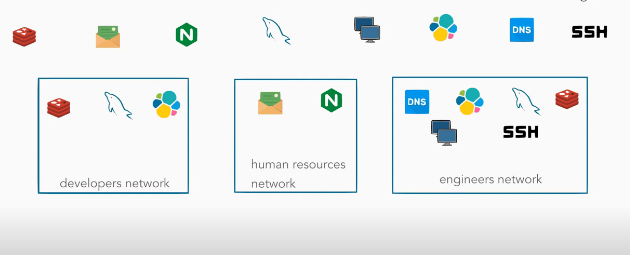
- Multiple virtual networks
You can group your applications as networks. And apply access policy to each of them. You can create a virtual network for the human resources group, , and another for remote developers, you can use the same application in different networks. Creating a new network is just a few clicks.
- Embedded DNS
Embedded DNS is working, when you connect to a virtual network, you can reach each service with their names
- Multiple Tunnel Protocol
We are supporting SSH Tunnels, Wireguard, and SSL Tunnels. Wireguard tunnels are a good choice for performance, SSH Tunnels are old traditional TCP secure channels and SSL Tunnels support agentless connectivity.
- IdP providers
We are supporting Local, SAML, OAuth2 protocols and Google, Linkedin, Azure AD, Okta, Auth0, CyberArk, JumpCloud, OneLogin, Ping Identity, and more... Also for MFA (Multi-factor authentication) needs, you can use OTP with Google Authenticator, Microsoft Authenticator or what you want. Also, we are supporting passwordless authentication.
- PKI Infrastructure
For IoT device authentication, machine authentication, and application authentication, you can use certificate-based authentication
- Ip Intelligence
We are supporting two types of IP Intelligence sources. You can subscribe ipdata.co, ipapi.com, ipify.org and get more details about connecting ip and applying different policies. Commercial sources provide ip details like Country, VPN , and Tor. Selecting only a limited country for a secure connection makes your system more secure. Or blocking Tor ips is a good choice
We are also supporting OSINT (open source intelligence lists), you can save lists as you need, and apply policy toeach of them
- Time-based access
Define time-based access rules to your virtual networks.
- Continuous monitoring
ZTNA is monitoring every network packet in our virtual networks. Every Ping, Dns, Udp, Tcp packet, etc... Always checking if connections are valid according to policies.
- Exporting data
Export data to ElasticSearch or SIEM options
FerrumGate ZTNA
FerrumGate applies all zero trust principles, with more features.