Zero Trust Endpoint Security - Device Posture Check
May 5 2023
What is Device Posture Check?
The device posture check is an important aspect of the Zero Trust security model, which assumes that no device or user should be trusted by default. By checking a device posture, zero trust networks can assure that only secure devices are allowed to access corporate resources.
We can say that this is the synonym of Network Access Control (NAC), in Zero Trust security model.
Before a device can access, we need to be sure that, the device meets the security standards and policies set by the organization.
Creating a Device Inventory?
This is also useful for collecting device information and creating an inventory. Following their status. Creating statistics about them over time.
Check List?
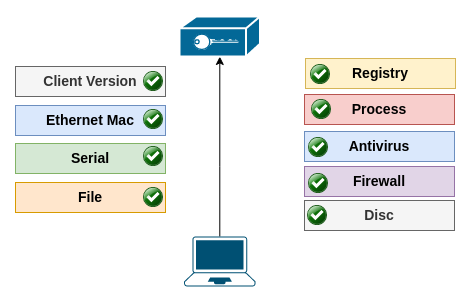
Let's look at, what we are checking in detail.
- Client version: We are connecting with secure tunnels to Zero Trust networks. And we can check this connected client version. This is useful for mitigating attack sources.
- Ethernet Mac: All connected devices have Mac addresses. Checking this address is an option.
- Serials: We are trying to get BIOS serial, if we can not get it, then trying to get install uuid. This is the device's long term ID for identifying the device.
- File: We can check if a file exits and check its SHA256 value.
- Registry: Checking a registry path can be used if a process is running or the connected device is yours.
- Process: Check if a process is running. And check its file SHA256 value, if it is infected or not
- Antivirus: Check if the client is using an active Antivirus software like Windows Antivirus.
- Firewall: Check if the client is using an active Firewall like Windows Defender.
- Encrypted Disc Check if client is using an encrypted disc.
Benefits
For remote working forces, Bring Your Own Device is a plus.
Limiting access from unhealthy devices to your corporate resources.
Continous monitoring every connected device.