Zero Trust IOT Connectivity
Apr 23 2023
IOT Connectivity
In the recent decades the rise of the Internet of Things (IoT) , has led to a new cyber security era. With these increased connectivities come increased security risks. And created a new attack surface for cybercriminals. Here zero trust connectivity comes in role. We will explore zero trust paradigm for IOT connectivity.
What is Zero Trust?
Zero Trust paradigm can be simplified as Never Trust, Always Verify. We explored more details in this article.
How Zero Trust Applies to IoT Connectivity Solutions
When it comes to IoT Connectivity Solutions, every device must be authenticated and authorized before being granted access to a network. This requires an IAM (Identity Access Management) solution, for identifying devices and applying policies for them.
In a zero trust environment, you can not trust any device, regardless of whether you own or a third-party device. And all devices must be authenticated before connecting to a network, resource, or application. And continue to monitor every action.
Benefits of Zero Trust for IoT Connectivity Solutions
FerrumGate applies all zero trust principles, with more features.
- More Security
By verifying and authorizing every access request, organizations can significantly reduce the risk of unauthorized access, data breaches, and other security threats.
- More Visibility
Monitor every request, every data manipulation, and every attempt action in the network.
- Better Flexibility
Compose virtual networks with your resources. Define policies for each of them.
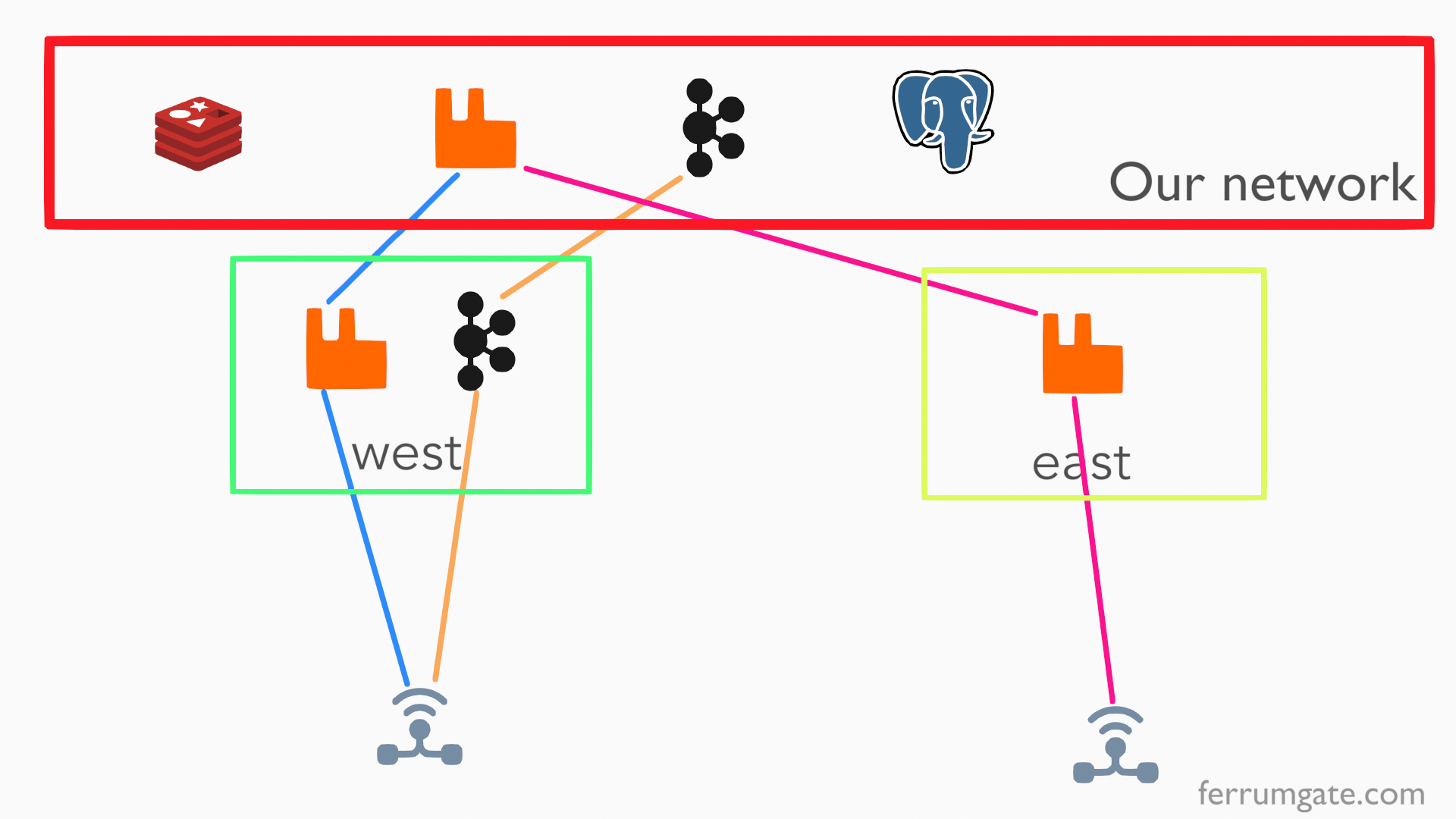
An Implementation Example
Let's imagine 2 locations (east, west) where your IOT devices connect and send data
And your network has services RabbitMQ, Kafka, Redis, Memcache Postgresql
You may need everything to be simple and more secure
- east devices can only reach RabbitMQ
- west devices can only reach RabbitMQ and Kafka
- you don't want to write code for authentication and authorization
- you don't want to care about secure connectivity, like SSL/TLS
just send data, don't care else
this is possible and so easy with our solution. Just create virtual networks as you want, apply certificate based authentication, see PKI and users for more.
This approach solves the below problems
- Secure Connection
- Device identity problem
- Zero Trust Access
- Logs